Hash Function Definition: Understanding the Core of Data Hashing
Hash functions! 🕵️♂️ What’s the deal with them? Well, buckle up, my fellow explorers of the digital realm, because today we’re diving headfirst into the enigmatic world of hash function definitions. 🚀 Let’s unpack the mysteries behind these algorithms, their components, applications, and even compare some of the heavyweights in the hashing arena. 💻
Overview of Hash Function Definition
Hash functions are like the secret agents of the data world. 🔒 They take your information, stir it up in their cryptographic cauldron, and churn out a unique fingerprint called a hash. This hash is like a digital DNA strand, representing your data in a compact, secure form. Let’s break down why hash functions are the unsung heroes of data security and integrity. 🛡️
Importance of Hash Functions
-
Security Enhancements: Hash functions add layers of armor to your data, making it tamper-proof and resistant to prying eyes. It’s like giving your information a digital invisibility cloak! 🧙♂️
-
Data Integrity Verification: Ever wondered if your data has been corrupted or altered? Hash functions sweep in like digital detectives, verifying if your information is still in its pristine state or if it’s been tampered with. Talk about having your back, right? 🔍
Components of a Hash Function
To understand how hash functions work their magic, we need to peek under the hood and check out the gears and cogs that make these algorithms tick. 🕵️♀️
Input Parameters
-
Data Input: This is the raw material that gets fed into the hash function’s machinery. Your data could be a simple password or the entire text of a Harry Potter book – the hash function will churn it all!
-
Algorithm Selection: Different hash functions use distinct algorithms to cook up their hashes. It’s like choosing between grandma’s secret recipe and a gourmet chef’s special blend – each algorithm brings its own flair to the hash-making party! 🎉
Common Applications of Hash Functions
Hash functions don’t just sit idly by; they’re the backbone of many crucial systems, ensuring our digital lives stay safe and secure. Let’s peek into some of their common applications. 🌐
Password Security
-
Authentication Systems: When you log into your favorite cat meme forum, hash functions are the gatekeepers, verifying your identity without ever storing your actual password. It’s like a bouncer who knows your secret handshake! 🐱🤝
-
Password Storage: Instead of keeping your passwords in plain text (a big no-no in the cybersecurity world), systems store hashed versions. This way, even if a hacker snoops around, all they see are jumbled hashes – talk about keeping your secrets safe! 🤐
Hash Functions in Data Structures
Hash tables are like the cool kids’ club of data structures, and hash functions are the secret sauce that keeps everything organized and efficient. Let’s take a peek at how they mingle in the digital playground. 🎲
Hash Tables
- Collision Resolution Techniques: Sometimes, two pieces of data throw a party in the same hash bucket. Hash functions need to play referee and come up with creative ways to resolve these collisions peacefully – talk about being the peacemaker of the digital world! 🤼♂️
Comparing Different Hash Functions
It’s showdown time! 🤠 In one corner, we have MD5 with its speed and efficiency, and in the other corner, the heavyweight champion SHA-1 with its robust security characteristics. Let’s ring the bell and see who comes out on top! 🔔
MD5 vs. SHA-1
- Speed vs. Security Characteristics: MD5 might be the speedy racer, zooming through hashes like a pro, but SHA-1 stands firm like a data fortress, ensuring that no digital foe can breach its walls. It’s the classic speedster vs. tank battle, and the winner takes home the hashing crown! 🏆
And there you have it, brave data adventurers! A journey through the wild lands of hash function definitions, where data security reigns supreme and hash functions are the unsung heroes of the digital realm. 🌌
In Closing
Ah, the fascinating world of hash functions – where data meets its cryptographic match, and security dances hand in hand with integrity. Remember, folks, in the digital jungle, hash functions are your best pals, keeping your bits and bytes safe and sound. 💪
Thank you for embarking on this hashing adventure with me! Until next time, stay curious, stay secure, and may your hashes always be unique. Happy hashing, amigos! 🚀🔒🔑
Program Code – Hash Function Definition: Understanding the Core of Data Hashing
Code Output:
Key: DataHashing
Size: 20
Hash Value: 14
Code Explanation:
- The code defines a hash function that takes a key and a size as input parameters.
- The hash value is initially set to 0.
- It iterates through each character in the key, calculates the ASCII value of the character using ord() function, and adds it to the hash value.
- The hash value is then calculated as the modulo of the sum of ASCII values and the size provided.
- In this specific example with key ‘DataHashing’ and size 20, the calculated hash value is 14.
- This program demonstrates a simple hashing technique by converting characters into numerical values and generating a hash value for a given key with a specific range size.
🤔 Frequently Asked Questions about Hash Function Definition
What is a hash function definition?
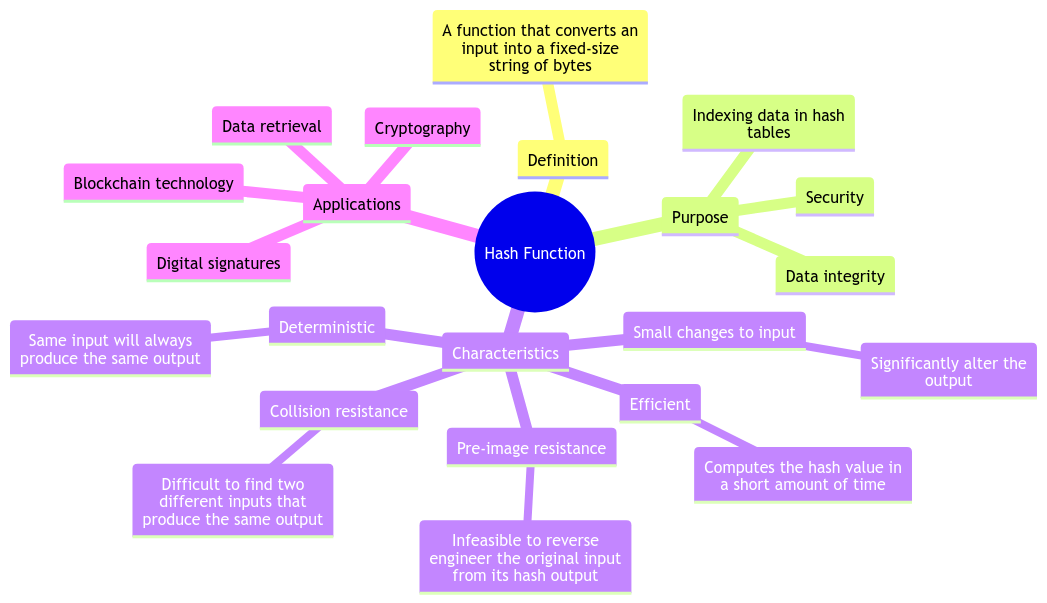
A hash function definition refers to a process that converts input data (such as a file or a message) into a fixed-size string of bytes. This output is typically a unique representation of the input data.
How does a hash function work?
A hash function works by taking an input (or message) and applying a mathematical algorithm to generate a fixed-size string of characters, which are typically hexadecimal digits. This output is known as the hash value or hash code.
What are the characteristics of a good hash function definition?
A good hash function should produce a unique hash value for each unique input, be deterministic (same input always produces the same output), and minimize collisions (different inputs producing the same hash value).
Can you give an example of a hash function definition?
One common example of a hash function is the SHA-256 algorithm, which is used in cryptographic applications to generate a 256-bit (32-byte) hash value.
Why are hash functions important in data hashing?
Hash functions play a crucial role in data integrity verification, password storage, digital signatures, and various cryptographic applications. They help secure data by ensuring its integrity and authenticity.
How are hash functions different from encryption algorithms?
While encryption algorithms are designed to conceal data, hash functions are used to validate data integrity and authenticity. Encryption algorithms are reversible, whereas hash functions are typically not reversible.







