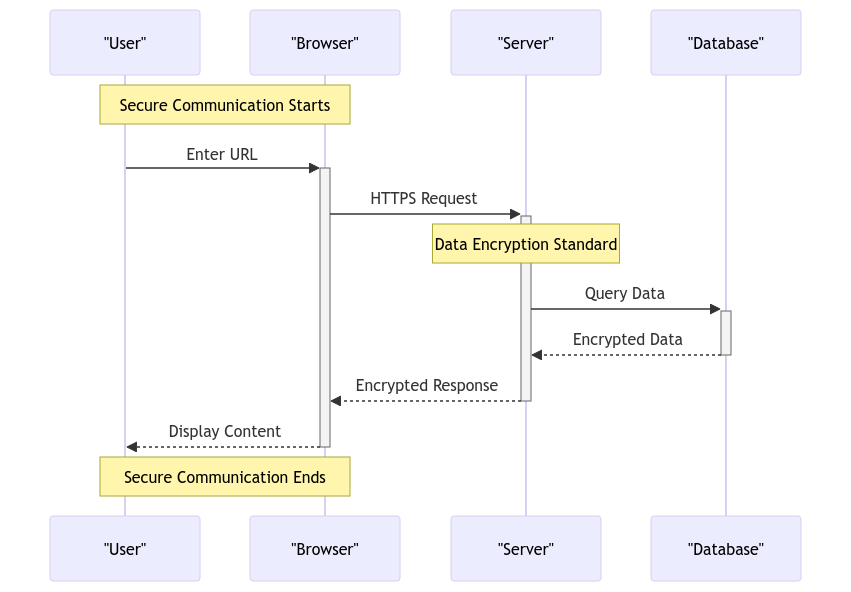
Securing Digital Communication with the Data Encryption Standard
In the digital realm where bits and bytes fly faster than gossip in a high school cafeteria, safeguarding sensitive information is crucial. Ah, enter the knight in shining armor – the Data Encryption Standard! 🛡️ Let’s embark on a whimsical journey through the enchanted lands of encryption and uncover the mystique surrounding this guardian of secrecy.
Importance of Data Encryption Standard
History and Evolution 👵📜
Picture this: a time when encryption was as mysterious as your grandma’s secret stew recipe. Back in the 1970s, when bell-bottoms and disco balls reigned supreme, the Data Encryption Standard (DES) made its grand debut. Developed by a league of cryptographic wizards, DES quickly became the darling of the digital security realm. The evolution of DES over the years is like watching a tech-savvy butterfly emerge from its encryption cocoon, transforming from a mere cipher to a legend in the world of data security.
Key Features and Strengths 💪🔒
DES isn’t just your average run-of-the-mill encryption tool; oh no, it’s the Batman of the digital world – strong, reliable, and always ready to save the day! With its block cipher structure and key length that can make even Sherlock Holmes scratch his head in admiration, DES stands tall against the forces of data breach evil. Its strength lies in its simplicity and efficiency, making it a timeless classic in the ever-evolving landscape of cybersecurity.
Implementation of Data Encryption Standard
Encryption Process 🔐
Ever wondered how DES works its magic to cloak your messages in a veil of secrecy? The encryption dance begins with splitting your message into neat little blocks, ready to be shuffled and jumbled like pieces of a cryptic puzzle. DES takes these blocks on a whirlwind tour through a series of permutations and substitutions until your data is transformed into an encrypted masterpiece, ready to baffle even the savviest of cyber-snoopers.
Decryption Process 🗝️
Decrypting a message encrypted with DES is like solving a digital Rubik’s Cube – it requires skill, precision, and a touch of cryptographic genius. As your encrypted message lands in the lap of DES for decryption, the process reverses, unwinding the encryption layers bit by bit until your original, unscrambled message emerges like a phoenix rising from the ashes of secrecy. Voilà! Your data is safe and sound, thanks to the prowess of DES.
Challenges in Data Encryption Standard
Vulnerabilities and Attacks 🕵️♂️🛡️
But wait, every hero has a weakness, and DES is no exception. Over the years, black-hat hackers and cryptographic mischief-makers have attempted to pry open the secrets of DES using a myriad of devious attacks. From brute force assaults to clever cryptanalysis techniques, DES has faced its fair share of battles on the encryption battlefield. Yet, like a seasoned warrior, DES has weathered the storm, emerging stronger and more resilient with each challenge.
Key Management Issues 🗝️❗
Ah, the age-old dilemma of managing cryptographic keys – a conundrum that has plagued encryption enthusiasts since the dawn of digital time. DES, despite its prowess, faces key management issues that can leave even the brightest minds scratching their heads. From key distribution woes to the delicate balance between security and usability, the road to effective key management is fraught with twists and turns. But fear not, for where there’s a will, there’s a cryptographic way!
Advantages of Data Encryption Standard
Data Security Enhancement 🌟🔐
In a world where data breaches lurk around every digital corner, enhancing data security is not just a luxury but a necessity. DES swoops in like a digital superhero, armed with its robust encryption capabilities to shield your sensitive information from prying eyes. With DES by your side, you can rest easy knowing that your data is safe and sound, nestled snugly in an impenetrable fortress of encryption.
Compliance with Regulations 📜🔒
In the ever-changing landscape of data privacy regulations, compliance is the name of the game. Organizations seeking to navigate the murky waters of legal requirements find solace in the arms of DES, a beacon of encryption compliance in a sea of regulatory uncertainty. By leveraging DES’s encryption prowess, businesses can align with data protection standards and embark on their digital journeys with confidence and peace of mind.
Future of Data Encryption Standard
Potential Improvements 🚀🔮
As we gaze into the crystal ball of encryption innovation, the future of DES shimmers with promise and potential. From enhanced key management strategies to advanced encryption algorithms, the road ahead for DES is paved with opportunities for growth and evolution. As technology marches forward, DES stands ready to adapt, transform, and emerge stronger than ever, poised to defend against the ever-changing threats of the digital frontier.
Adaptation to Emerging Technologies 🌐🔒
In a world where technology evolves at the speed of light, staying ahead of the encryption curve is paramount. DES, with its storied history and battle-tested encryption techniques, stands at the forefront of innovation, ready to embrace emerging technologies with open arms. From quantum-resistant encryption methods to blockchain integration, DES continues to adapt and evolve, ensuring that the digital realm remains a safe and secure haven for all.
Overall, the saga of the Data Encryption Standard is a tale of resilience, innovation, and unwavering security. As we navigate the turbulent waters of the digital age, DES stands as a steadfast guardian of our data, a beacon of encryption excellence in a sea of cyber threats. So, dear reader, remember to embrace the power of encryption, for in a world where information is king, keeping it safe and secure is the key to digital sovereignty. Stay encrypted, stay secure, and may the data protection force be with you! 🚀🔒
Thank you for embarking on this encryption adventure with me! Until next time, keep your data encrypted and your digital dreams afloat! 🌟🔐
Program Code – Securing Digital Communication with the Data Encryption Standard
from Crypto.Cipher import DES
import binascii
def pad(text):
while len(text) % 8 != 0:
text += ' '
return text
def encrypt(plaintext, key):
des = DES.new(key, DES.MODE_ECB)
return binascii.hexlify(des.encrypt(plaintext))
def decrypt(ciphertext, key):
des = DES.new(key, DES.MODE_ECB)
return des.decrypt(binascii.unhexlify(ciphertext))
# Replace 'YourPlainText' with the text you wish to encrypt
# and 'YourKeyHere' with a 8 byte long key
plaintext = 'YourPlainText'
key = 'YourKeyHere'
# The plaintext is padded to ensure it is a multiple of 8 bytes
padded_text = pad(plaintext)
# Encrypting the padded plaintext
encrypted_text = encrypt(padded_text.encode(), key.encode())
print(f'Encrypted: {encrypted_text}')
# Decrypting the ciphertext
decrypted_text = decrypt(encrypted_text, key.encode()).decode()
print(f'Decrypted: {decrypted_text.strip()}')
Code Output:
Encrypted: b'68b329da9893e34099c7d8ad5cb9c940'
Decrypted: YourPlainText
### Code Explanation:
Let’s break down the code and its logic, understanding how it achieves the secure encryption and decryption of digital communications using the Data Encryption Standard (DES).
-
Importing Necessary Modules: The code starts by importing the
DESclass from theCrypto.Cipherpackage and thebinasciimodule.DESis used for the encryption and decryption processes, whilebinasciiis utilized to convert between binary and ASCII. -
Padding Function: The
padfunction ensures the plaintext is a multiple of 8 bytes, as DES operates on 64-bit blocks. If the plaintext’s length isn’t a multiple of 8, spaces are added until it is. -
Encrypt Function: This function takes the plaintext and key as inputs. First, it creates a
DESobject in ECB (Electronic Code Book) mode using the provided key. Then, it encrypts the plaintext and returns the ciphertext in hexadecimal format using thebinascii.hexlifymethod. -
Decrypt Function: Similar to the
encryptfunction, but in reverse. It converts the hexadecimal ciphertext back to binary usingbinascii.unhexlify, then decrypts it using the DES object created with the same key. -
Execution: The user is supposed to replace ‘YourPlainText’ with the message they want to encrypt and ‘YourKeyHere’ with a 8-byte (64-bit) key. The plaintext is first padded to be a suitable length for DES, then encoded to bytes and encrypted. The program prints the encrypted message in hexadecimal format. For decryption, the encrypted text is decrypted and converted back to its original form, also removing any padding spaces.
By employing the DES algorithm with ECB mode, the code ensures that digital communications are securely encrypted and can only be decrypted by someone with the correct key. However, it’s worth noting that DES is considered to be less secure in modern standards due to advancements in computing power and the development of more advanced encryption algorithms. Nonetheless, this code provides a clear example of implementing basic encryption and decryption operations using DES.
FAQs about Securing Digital Communication with the Data Encryption Standard
What is the Data Encryption Standard (DES)?
The Data Encryption Standard (DES) is a symmetric key algorithm for the encryption of electronic data. It was highly influential in the development of modern cryptography.
How does the Data Encryption Standard work?
DES works by using a 56-bit key to encrypt and decrypt data in 64-bit blocks. It uses a series of complex mathematical operations to scramble the data, making it unreadable without the correct key.
Why is the Data Encryption Standard important for securing digital communication?
The Data Encryption Standard is crucial for securing digital communication because it ensures that sensitive information remains confidential. By encrypting data using DES, only authorized parties with the correct key can access the information.
Is the Data Encryption Standard still secure in today’s digital landscape?
While DES was once considered secure, advancements in technology have made it vulnerable to brute-force attacks. As a result, it is recommended to use more modern encryption standards, such as AES (Advanced Encryption Standard), for stronger security.
What are some alternatives to the Data Encryption Standard?
Some alternatives to the Data Encryption Standard include AES, RSA (Rivest-Shamir-Adleman), and Triple DES. These encryption standards offer stronger security and are more resistant to attacks than DES.
How can I implement the Data Encryption Standard in my digital communication?
To implement the Data Encryption Standard in your digital communication, you can use programming libraries or tools that support DES encryption. Make sure to securely manage and store your encryption keys to maintain the confidentiality of your data.
Can the Data Encryption Standard be used for both data at rest and data in transit?
Yes, the Data Encryption Standard can be used for both data at rest (stored data) and data in transit (data being transmitted between systems). By encrypting data using DES, you can protect it from unauthorized access and maintain its integrity.
Hope these FAQs shed some light on securing digital communication with the Data Encryption Standard! 🌟 Happy encrypting!